Oligo Security researchers have uncovered a critical vulnerability, named "0.0.0.0 Day," that has been present for 18 years and impacts all major web browsers, including Chromium, Firefox, and Safari.
What is 0.0.0.0 Day
This flaw allows malicious websites to bypass browser security measures and communicate with services on an organization's local network, potentially leading to unauthorized access and remote code execution by external attackers.
The root cause of this issue lies in the inconsistent implementation of security mechanisms across different browsers and a lack of standardization within the browser industry.
The IP address 0.0.0.0, typically used as a placeholder or default address, can be exploited by attackers to access local services, including those related to development, operating systems, and internal networks.
How can 0.0.0.0 Day Affect you
The implications of the 0.0.0.0 Day vulnerability are significant, affecting both individuals and organizations. Attackers can potentially bypass browser security to access sensitive services on local devices, leading to unauthorized access, data breaches, and remote code execution.
A bug report from 2006 highlighted the longstanding problem of browsers allowing requests to be sent to local or internal networks from less-private contexts. Despite numerous discussions and attempts to prioritize the issue, the bug remains unresolved.
The lack of standardization in the browser industry has contributed to the inconsistent implementation of security mechanisms, resulting in vulnerabilities like 0.0.0.0 Day.
How does 0.0.0.0 Day bypass Browser Security
To fully grasp this vulnerability, it's crucial to understand browser security and the role of IP addresses like 0.0.0.0.
Browsers have long been targets for security threats, which has led to the introduction of advanced security concepts such as sandboxing and HTTPS-ONLY cookies.
The IP address 0.0.0.0 is used in various contexts, including as a placeholder or default address. However, while it is prohibited as a destination address in IPv4, it is permitted as a source address in specific situations.
Despite these restrictions, 0.0.0.0 has been used in various contexts, such as in /etc/hosts files to block certain domains or in networking policies to allow access to all IPs.
Fingerprinting website users is a well-known technique used for purposes like identifying returning users. However, threat actors can exploit this technique to gather intelligence for phishing campaigns.
Using the 0.0.0.0 Day vulnerability, attackers can perform port scans on users, potentially identifying open ports and vulnerable services.
Google’s Private Network Access (PNA) initiative seeks to enhance CORS by restricting websites from sending requests to servers on private networks. PNA aims to differentiate between public, private, and local networks to prevent requests from being sent to more secure contexts.
According to the current PNA specification, the following IP segments are considered private or local:
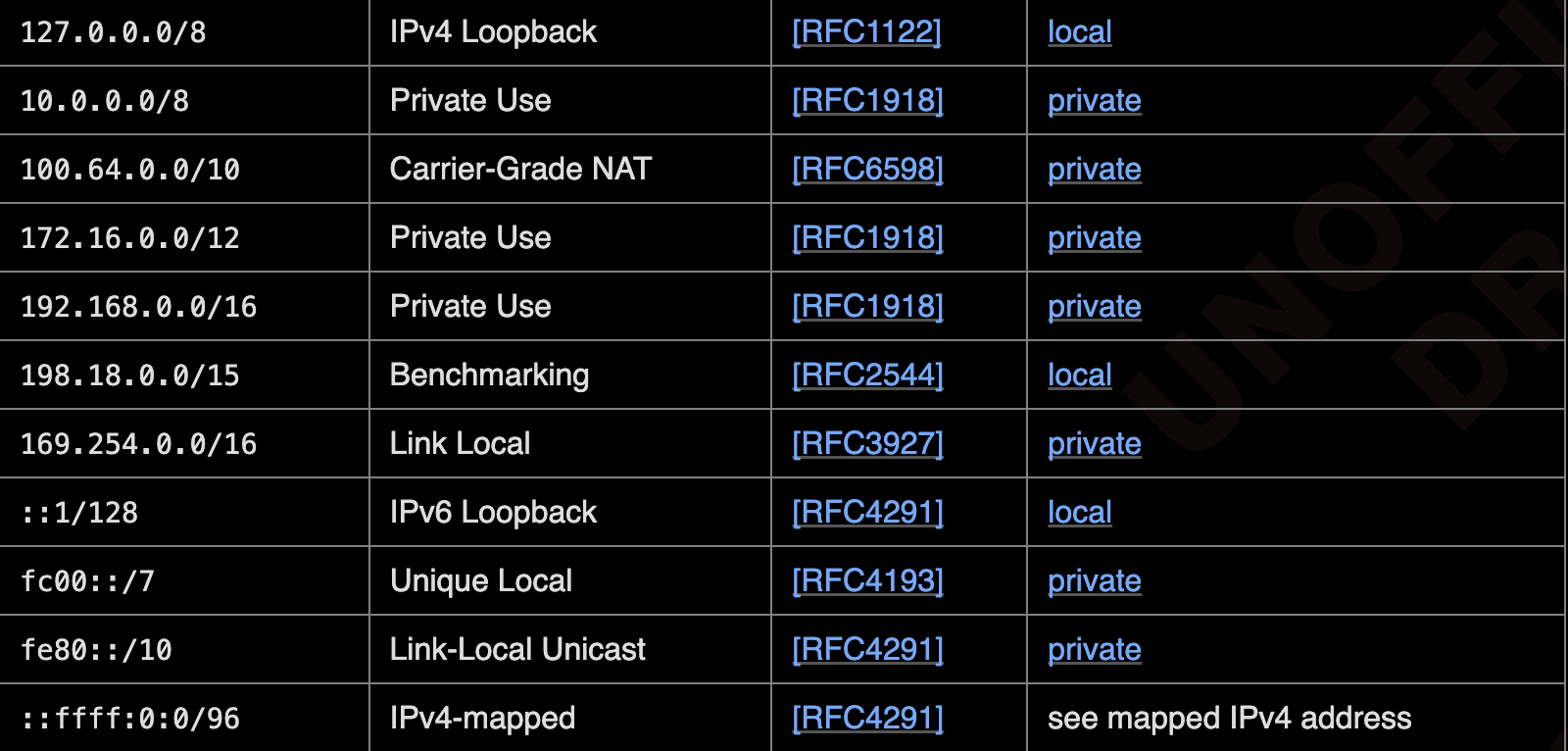
Oligo Researchers discovered that 0.0.0.0 was not classified as a private or local IP segment, enabling websites to send requests to 0.0.0.0.
Following responsible disclosure, the bypass of the current PNA implementation and the inherent flaws in browsers were reported to all major browsers.
Several applications are likely affected by the 0.0.0.0 Day vulnerability. Oligo Security researchers identified several vulnerable applications, including Ray, Selenium Grid, and Pytorch Torchserve (ShellTorch), which could be exploited through 0.0.0.0, leading to remote code execution and unauthorized access.
After responsible disclosure, browser vendors acknowledged the security flaw and are working on implementing browser-level mitigations:
Google Chrome (and Chromium-based browsers like Edge)
- PNA Initiative: Evolving Private Network Access (PNA) led by Google.
- Vulnerability: 0.0.0.0 bypasses PNA, allowing access to private IPs.
- Fix Rollout: Blocking 0.0.0.0 from Chrome 128, fully effective by Chrome 133.
- Statistics: 0.015% of websites (around 100K) communicate with 0.0.0.0.
Apple Safari
- WebKit Changes: Now blocks 0.0.0.0 access.
- Implementation: Requests to all-zero IP addresses are blocked.
Mozilla Firefox
- Current Status: No immediate fix; PNA not initially implemented.
- Specification Update: Fetch specification updated to block 0.0.0.0.
- Future Plans: Implementation of PNA will eventually block 0.0.0.0.
The 0.0.0.0 Day vulnerability underscores the importance of standardizing practices across the browser industry and fully implementing Private Network Access (PNA) according to those standards. Until PNA is fully deployed, public websites can still use JavaScript to send HTTP requests to local network services, which could result in unauthorized access and remote code execution.